Interactive proof system
|

Adiparwa versi Jawa Kuno yang diterbitkan oleh Dinas Pendidikan Provinsi Bali. Adiparwa (bahasa Sanskerta: आदिपर्व, Ādiparva) adalah buku pertama atau bagian (parwa) pertama dari kisah Mahabharata. Pada dasarnya bagian ini berisi ringkasan keseluruhan cerita Mahabharata, kisah-kisah mengenai latar belakang cerita, nenek moyang keluarga Bharata, hingga masa muda Korawa dan Pandawa). Kisahnya dituturkan dalam sebuah cerita bingkai dan alur ceritanya meloncat-loncat sehingga tidak me…

BMXStruktur yang tersediaPDBPencarian Ortolog: PDBe RCSB Daftar kode id PDB2EKX, 2YS2, 3SXR, 3SXSPengidentifikasiAliasBMX, ETK, PSCTK2, PSCTK3, BMX non-receptor tyrosine kinaseID eksternalOMIM: 300101 MGI: 1101778 HomoloGene: 20411 GeneCards: BMX Lokasi gen (Tikus)Kr.X chromosome (tikus)[1]PitaX|X F5Awal162,975,838 bp[1]Akhir163,041,189 bp[1]Pola ekspresi RNAReferensi data ekspresi selengkapnyaOntologi genFungsi molekuler• transferase activity• nucleotide bi…

Beauty and the BeastPoster TeatrikalSutradaraChristophe GansProduserRichard GrandpierreDitulis olehChristophe GansSandra Vo-AnhBerdasarkanSi Cantik dan Buruk Rupa olehGabrielle-Suzanne Barbot de VilleneuvePemeranVincent CasselLéa SeydouxAndré DussollierPenata musikPierre AdenotSinematograferChristophe BeaucarnePenyuntingSébastien PrangèrePerusahaanproduksiEskwadPathéStudio BabelsbergDistributorPathéTanggal rilis 12 Februari 2014 (2014-02-12) (Prancis) 14 Februari 2014&#…

Cari artikel bahasa Cari berdasarkan kode ISO 639 (Uji coba) Kolom pencarian ini hanya didukung oleh beberapa antarmuka Halaman bahasa acak Bahasa Numidia Timur Libya Kuno Dituturkan diProvinsi Numidia dan AfrikaEtnisMaesuliaEraSekitar 200 SM Rumpun bahasaAfroasiatik ? Libiko-BerberNumidia Timur Sistem penulisanLibiko-Berber (Proto-Tifinagh)Kode bahasaISO 639-3nxmLINGUIST ListnxmGlottolognumi1241[1] Status konservasi Punah EXSingkatan dari Extinct (Punah)Terancam CRSingk…

Taken 2Theatrical release posterSutradaraOlivier MegatonProduserLuc BessonDitulis olehLuc BessonRobert Mark KamenPemeranLiam NeesonMaggie GraceFamke JanssenRade ŠerbedžijaPenata musikNathaniel Méchaly [fr]SinematograferRomain LacourbasPenyuntingCamille DelamarreVincent TabaillonPerusahaanproduksiEuropaCorpGrive ProductionsCanal+M6 FilmsCiné+Dune EntertainmentDistributor20th Century Fox (US) EuropaCorp (France)Tanggal rilis 07 September 2012 (2012-09-07) (Deauville…

Location of Cass County in Indiana This is a list of the National Register of Historic Places listings in Cass County, Indiana. This is intended to be a complete list of the properties and districts on the National Register of Historic Places in Cass County, Indiana, United States. Latitude and longitude coordinates are provided for many National Register properties and districts; these locations may be seen together in a map.[1] There are 16 properties and districts listed on the Nation…

Untuk provinsi yang bernama sama, lihat Provinsi Santiago de Cuba.Santiago de CubaMunisipalitasNegaraKubaProvinsiSantiago de CubaBerdiri1514Luas • Total1.023,8 km2 (3,953 sq mi)Ketinggian82 m (269 ft)Populasi (2004)[1] • Total472.255 • Kepadatan461,3/km2 (11,950/sq mi)Kode area telepon+53-22Situs webSantiago.cu Santiago de Cuba adalah sebuah kota di Kuba yang merupakan ibu kota provinsi Santiago de Cuba, 870 kilometer…
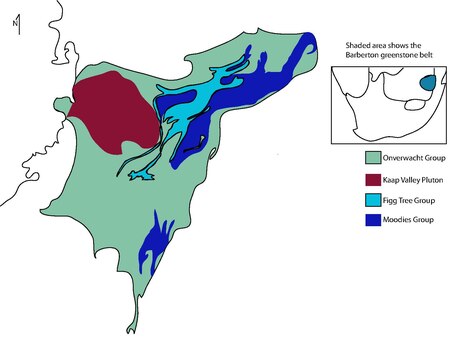
Ancient granite-greenstone terrane in South Africa Location of the Barberton Greenstone Belt. The Barberton Greenstone Belt is situated on the eastern edge of the Kaapvaal Craton in South Africa. It is known for its gold mineralisation and for its komatiites, an unusual type of ultramafic volcanic rock named after the Komati River that flows through the belt. Some of the oldest exposed rocks on Earth (greater than 3.6 Ga) are located in the Barberton Greenstone Belt of the Eswatini–Barberton a…

Canadian evolutionary psychologist Gad SaadSaad in 2010Born (1964-10-13) 13 October 1964 (age 59)Beirut, LebanonNationalityLebanese, CanadianEducationMcGill University (BSc, MBA)Cornell University (MSc, PhD)Scientific careerFieldsMarketing, consumer behaviourInstitutionsConcordia UniversityThesisThe adaptive use of stopping policies in sequential consumer choice (1994)Doctoral advisorEdward Russo YouTube informationChannel GadSaad Subscribers298 thousand[1]Total views33.37…

Mandarin Oriental Hotel GroupMandarin Oriental JakartaJenisUmum (SGX: M04 LSE: MDO)IndustriPenginapan, pariwisataDidirikan1963; 61 tahun lalu (1963)Kantorpusat33-35 Reid Street, Hamilton, BermudaCabang38 (2024)ProdukHotelPendapatanUS$404 juta (2006)Laba operasiUS$122 juta (2006)Laba bersihUS$80 juta (2006)IndukJardine MathesonSitus webwww.mandarinoriental.com Mandarin Oriental Hotel Group (MOHG) adalah perusahaan perhotelan yang merupakan anak usaha Jardine Matheson. Didirikan di Hong Kong …
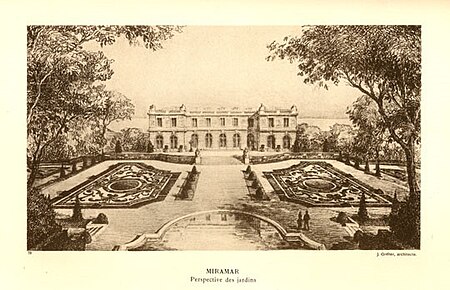
Private residence in Rhode Island, USMiramarPostcard image of Miramar circa 1915General informationTypePrivate residenceArchitectural styleFrench neoclassicalLocationAquidneck Island, Newport, Rhode Island, USAddress646 Bellevue AvenueCoordinates41°27′30″N 71°18′17″W / 41.458285°N 71.304767°W / 41.458285; -71.304767Construction started1911Completed1915InauguratedAugust 20, 1915ClientGeorge & Eleanor Elkins WidenerTechnical detailsFloor count3Floor area30,0…

Bride WarsPoster bioskopSutradaraGary WinickProduserKate HudsonMatt LuberAlan RichePeter RicheJulie YornDitulis olehGreg DePaulJune RaphaelCasey WilsonKaren McCullah LutzKirsten SmithPemeranKate HudsonAnne HathawayCandice BergenChris PrattBryan GreenbergSteve HoweyKristen JohnstonPenata musikEdward ShearmurPerusahaanproduksiRegency EnterprisesNew RegencyFirm FilmsDistributor20th Century FoxTanggal rilis9 Januari 2009Durasi89 menitNegaraAmerika SerikatBahasaInggrisAnggaran$30 jutaPendapatan…

هذه المقالة عن العقلانية في الفلسفة. لمفاهيم أخرى للعقلانية، طالع عقلانية (توضيح). عقلانيةمعلومات عامةجزء من مصطلحات علم النفس النقيض تجريبية تعديل - تعديل مصدري - تعديل ويكي بيانات رينيه ديكارتباروخ سبينوزاغوتفريد لايبنتس في الفلسفة، العقلانية هي النظرة المعرفية ال…

Chemical compound EA-3580Identifiers IUPAC name (1-methylpiperidin-4-yl) 2-cyclobutyl-2-hydroxy-2-phenylacetate CAS Number54390-94-2 YPubChem CID171342ChemSpider149791UNIIRF3SNA5PA2CompTox Dashboard (EPA)DTXSID30969510 Chemical and physical dataFormulaC18H25NO3Molar mass303.402 g·mol−13D model (JSmol)Interactive image SMILES c3ccccc3C(O)(C2CCC2)C(=O)OC1CCN(C)CC1 InChI InChI=1S/C18H25NO3/c1-19-12-10-16(11-13-19)22-17(20)18(21,15-8-5-9-15)14-6-3-2-4-7-14/h2-4,6-7,15-16,21H,5,8-13H2,1H…

Marcello Lippi Lippi nel 2010 Nazionalità Italia Altezza 182 cm Peso 78 kg Calcio Ruolo Allenatore (ex difensore) Termine carriera 1982 - giocatore22 ottobre 2020 - allenatore Carriera Giovanili 1963-1969 Viareggio Squadre di club1 1969 Sampdoria0 (0)1969-1970→ Savona21 (2)1970-1979 Sampdoria274 (5)1979-1981 Pistoiese45 (0)1981-1982 Lucchese23 (0) Nazionale 1971 Italia U-232 (0) Carriera da allenatore 1982-1985 SampdoriaGiovanili1985-1986 Pontede…

Voce principale: Unione Sportiva Dilettantistica Arezzo. Unione Sportiva ArezzoStagione 1971-1972 Sport calcio Squadra Arezzo Allenatore Dino Ballacci Presidente Luigi Montaini Serie B15º posto Coppa ItaliaPrimo turno Maggiori presenzeCampionato: Tonani (38) Miglior marcatoreCampionato: Incerti (9) 1970-1971 1972-1973 Si invita a seguire il modello di voce Questa voce raccoglie le informazioni riguardanti l'Unione Sportiva Arezzo nelle competizioni ufficiali della stagione 1971-1972. Indic…

Reform Jewish synagogue in San Rafael, California, US This article uses bare URLs, which are uninformative and vulnerable to link rot. Please consider converting them to full citations to ensure the article remains verifiable and maintains a consistent citation style. Several templates and tools are available to assist in formatting, such as reFill (documentation) and Citation bot (documentation). (September 2022) (Learn how and when to remove this template message) Congregation Rodef SholomThe …

2020 US science fiction thriller film by Adam Mason SongbirdTheatrical release posterDirected byAdam MasonWritten by Adam Mason Simon Boyes Produced by Michael Bay Marcei A. Brown Jason Clark Jeanette Volturno Adam Goodman Andrew Sugerman Eben Davidson Starring KJ Apa Sofia Carson Craig Robinson Bradley Whitford Peter Stormare Alexandra Daddario Paul Walter Hauser Demi Moore CinematographyJacques JouffretEdited byGeoffrey O'BrienMusic byLorne BalfeProductioncompanies Invisible Narratives Platinu…

Constituency of Madhya Pradesh legislative assembly in India Indore-2Constituency No. 205 for the Madhya Pradesh Legislative AssemblyConstituency detailsCountryIndiaRegionCentral IndiaStateMadhya PradeshDistrictIndoreLS constituencyIndoreEstablished1967ReservationNoneMember of Legislative Assembly16th Madhya Pradesh Legislative AssemblyIncumbent Ramesh Mendola PartyBharatiya Janta Party Indore-2 Assembly constituency is one of the 230 Vidhan Sabha (Legislative Assembly) constituencies of Madhya …

MöslestadionThe Möslestadion in FreiburgLocationFreiburg, GermanyCapacity5,400 (1000 in covered seating area)SurfaceGrassConstructionOpenedOctober 1st, 1922RenovatedJune–August, 2013TenantsSC Freiburg second men's teamFreiburg Soccer SchoolSC Freiburg (women) The Möslestadion is a soccer stadium in Freiburg im Breisgau. The stadium used to be home to the Freiburger FC. Today it is used by the second men's team and the Freiburg soccer school of the SC Freiburg. Since the 2008/09 season, the …




![{\displaystyle \Pr[(\perp ,({\text{accept}}))\gets ({\tilde {\mathcal {P}}})(y)\leftrightarrow ({\mathcal {V}})(y)]<\epsilon .}](https://wikimedia.org/api/rest_v1/media/math/render/svg/89775f36bd79764d20bcbb10051edc1470cf8baa)









